Drone, Inc. - D. Phone Tracking
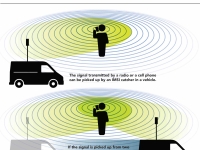
Nearly all mobile communication devices are designed to be tracked. A cell phone carrier, for instance, must generally know where all phones and towers in its network are at any given time. Otherwise a call placed in Karachi couldn’t be directed through the network to its receiving phone in Paris.
The military understands and exploits this. It knows that mobile phones send signals every few seconds looking for nearby towers so they can be reached. Every time a cell phone pings a tower, the tower creates a record of that connection and tells the rest of the network. Thus intelligence agencies monitoring the network infrastructure, or receiving information from the service provider, can use this information to track phones as they transit tower coverage zones, known as “cells,” around the world.
Even with access to that information, though, it is still a surprisingly difficult task to find the exact location of a cell phone. Cells can extend for miles and, contrary to popular belief, connecting to a given tower is not always an indication that a phone is within that cell.
Despite this, U.S. police routinely use mobile phone records to justify arrests. “Prosecutors often present those records as if they were DNA,” Douglas Starr, the co-director of the graduate program in science journalism at Boston University, wrote in the New Yorker magazine. “Designed for business and not tracking, call-detail records provide the kind of information that helps cell companies manage their networks, not track phones.60
Although it seems logical that a mobile phone would automatically connect to the closest tower, that’s not always the case. Instead it sends a radio message to all the local towers it can find. At a regional switching center, special software routes a call by checking a host of factors: the phone’s signal strength, the local weather, and what towers are shut for maintenance. Each mobile phone tower maintains a visitor location register, but there’s no guarantee that the phone was actually close to it.
“Your phone wants the clearest tower,” Michael Cherry, a former Bell Labs and NASA consultant who testifies on the science of cell-tower data in U.S. courts, said in an interview. 61 “But the clearest tower might not be the nearest tower, or even the tenth-nearest tower.”
61 “But the clearest tower might not be the nearest tower, or even the tenth-nearest tower.”
“The system is so fluid that you could sit at your desk, make five successive cell calls and connect to five different towers,” adds Starr. “The switching center may look for all sorts of factors, most of which are proprietary to the company’s software. The only thing that you can say with confidence is that I have connected to a cell site somewhere within a radius of roughly twenty miles.” That’s a little like knowing which county a house is located in but not knowing which town, let alone the street address.
In order to track mobile phones, the military uses radio locating devices known as IMSI catchers together with specialized software to conduct “geolocation,” i.e., the capability to locate a phone on a map. We’ll discuss IMSI catchers first and then address geolocation software in a later section.
IMSI Catchers
An IMSI (international mobile subscriber identity) catcher works by the simple expedient of pretending to be a mobile phone tower and inviting all phones in the area to connect with it. Hackers have designed basic IMSI catchers for under $100.62
While the fake tower can easily get a list of all the mobile phones in range, it can only approximate, based on signal strength, how far away each connected phone is. If the IMSI catcher also has a “direction finding” antenna, it may be able to guess the rough direction that a signal came from. Mountains, buildings, and other objects can further degrade reception.
In theory, a strong signal from at least three different phone towers can allow a phone to be located. But even then, reverse-engineering a user’s location from signal strength, direction and geography requires complex mathematical equations and computer algorithms.63
These techniques are extremely sensitive to measurement errors. In fact, the U.S. emergency phone system’s mobile tracking accuracy rates are sometimes as low as 10 percent.64
Military drones also map local wireless access points such as WiFi routers to help further track targets. A document revealed by National Security Agency (NSA) whistleblower Edward Snowden gives one example of NSA attempts to map such devices in Oman in March 2012: “Flights and targets were coordinated with both CIAers and NSAers. The mission lasted 6 months, during which 43 flights were flown,” an NSA staffer wrote about a mission code named Victorydance. “It was truly a joint interagency effort between CIA and NSA.”65
Global Positioning System Smart phones typically contain two radios. In addition to the receiver/transmitter that works on GSM or CDMA networks and allows users to exchange calls, text messages, and other data via local mobile phone towers, a smart phone also has a one-way GPS receiver that helps the phone locate itself. The Global Positioning System (GPS) is an array of 31 satellites that orbit the earth and regularly send out two indispensable bits of data: each satellite’s exact location and an exact timestamp, maintained by synchronized atomic clocks within each GPS satellite.72 Thus anywhere on Earth, a smartphone can pick up at least three such satellite signals to mathematically calculate its position accurately using trilateration—a more sophisticated version of triangulation. Newer phones combine GPS data with local WiFi signals, local mobile phone tower data, and even Bluetooth to calculate locations faster.73 Since a GPS device is only a receiver, i.e. for a user – be it a phone owner, a vehicle or a drone – to find their own location, it is not able to transmit its location to anyone else. However, when a smartphone user enables location sharing, this GPS data can be shared with apps via the second radio in the phone and used to calculate directions or nearby places of interest from cached databases. And while GPS location data could theoretically be hacked, this does not affect most users in Afghanistan and Yemen who have not historically used smartphones or GPS devices. |
But, as security experts note, this mapping is not an exact science since routers get moved, weather patterns disrupt signals, and phone towers have to be fixed. “If Google or Facebook get a physical location wrong, they show someone an ad for a restaurant they’re nowhere near,” Bruce Schneier, a security researcher, writes in The Atlantic magazine. “If the NSA gets a physical location wrong, they call a drone strike on innocent people.”66
Indeed, no less an authority than the Federal Bureau of Investigation (FBI) warns its agents to be careful of relying on mobile phone trackers. “Using the results as evidence is generally discouraged because of the level of technical expertise required to effectively operate the equipment,” an internal agency manual obtained by The Intercept states. “Accordingly, FBI employees should corroborate and verify the information obtained through other means.”67
Prices and technical details of many of such devices were listed in a leaked “secret surveillance catalogue” recently published by The Intercept. Two IMSI catcher gadgets used on Predators or Reapers are the Airhandler and Gilgamesh, both made by the Nevada-based Sierra Nevada Corporation. Gilgamesh forces mobile phones within range to connect with it. Airhandler, meanwhile, serves as the antenna system for Gilgamesh, while also capturing signals from push-to-talk radios in the process. Both upload data to NSANet, a parallel Internet system managed by the NSA.68
Another device for detecting and geolocating wireless signals is the T-Pod, made by U.K.-based BAE Systems. It consists of several IMSI catchers in a pod and is used on piloted aircraft as well as Reaper drones but is too heavy for a Predator to carry.69
One U.S. manufacturer of IMSI catchers, Florida-based Harris, sells its Stingray to dozens of police forces around the country, according to documents uncovered by the American Civil Liberties Union.70 Other Harris devices include Gossamer (a small hand-held device), Hailstorm, Kingfish, and Triggerfish, which retail for as much as $169,000, together with special antennas and amplifiers named Amberjack and Harpoon respectively.71
< Previous • Report Index • Download Report • FAQ/Press Materials • Watch Video • Next >



