Drone, Inc. - G. Geolocation
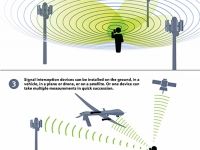
Target phone tracking also uses algorithms. When an IMSI catcher detects phones within range, it simply indicates that a device is located within a given radius. But for observers to exactly locate a mobile phone user requires certain methods, most of which use multiple, geographically separate sensors and calculation algorithms.
Drones and other surveillance aircraft carry IMSI catchers that collect information about intercepted signals like the direction, or angle, it arrived from, the exact time it arrived and the signal’s frequency. Each measurement provides valuable information for calculating the estimated location of phones.
The most common geolocation method is called "direction finding." It relies on the first measurement described above, "angle of arrival." That angle is measured at different sensors, or at the same moving sensor as it "hears" the signal at different locations over time. Straight lines are then drawn out toward the point where the signal came from, and where those lines intersect is believed to be the location of the phone or radio. Algorithms performing this calculation can be as simple as plotting those lines on a map or using least squares error estimation and discrete probability density methods.102
A more novel, and problematic, method of geolocation is known as Time-or-Frequency-Difference-of-Arrival (T/F DOA) which calculates the location of a phone or radio based on signal frequency as measured the difference in arrival time or at different sensors.103
The resulting estimates can only be approximate because the drones are moving, and often the phones are too. Indeed, all geolocation methods rely on relative measurements — estimating where the phone or radio is in relation to the known locations of the sensors. Accuracy therefore drops with "positioning errors (how well the aircraft knows its own position), signal measurement errors (how well the receiver can capture the received signal), and noise inherent in the signal," Kimberly Hale, an Air Force research analyst, writes in her 2012 Pardee Rand graduate school PhD dissertation on drones and geolocation.104
For example, pilots rarely have an exact lock on the location of drones since their on-board GPS can only provide latitude and longitude, but not the drone’s exact altitude or the angle of travel. A drone with a badly calibrated gyroscope (used to stabilize the aircraft) or a relay satellite that has drifted even slightly off course can throw off calculations, as can a phone signal that has bounced off buildings or mountains.
Locating the sources of radio signals has long been a military goal. Guardrail, one of the key predecessors of modern phone geolocation systems, was first used in Germany in 1971 to monitor Soviet troop movements in Eastern Europe. Still in use today, Guardrail employs three piloted Beechcraft C-12 Huron aircraft flying in orchestrated patterns to intercept selected low-, mid-, and high- band radio signals.105 Data from the three aircraft are sent back to ground stations, which then calculate the location of the "emitter."
Unfortunately, flying multiple drones in orchestrated patterns is not easy when the pilots are on the other side of the world. Rather than rely on three imperfect drone readings, then, analysts sometimes request help from the National Reconnaissance Office’s (NRO) dedicated military satellites.
The details of such support are not public, but there is some evidence it might come from a secretive program: Airborne Overhead Cooperative Operations (AOCO).
"AOCO helps … provide the warfighter with near real-time, enhanced geolocations on high-priority tactical missions," Frank Calvelli, the NRO principal deputy director, told a U.S. Congressional hearing in March 2016.106 "In 2015, AOCO improved geolocation accuracy by 75 percent over single sensors, and reduced specific mission planning analysis times by 90 percent." An NSA document leaked by Edward Snowden and published in The Intercept, also suggests that the NRO’s Mission 7600 satellites can collect phone locations.107 (These satellites also help spy on Middle East internet cafes, which rely on VSAT dish systems. In places where mobile data is slow, these cafes are sometimes the only way to get online.)
Modeling A Better System
Literature on the accuracy of drone geolocation of phones is somewhat sparse because of the clandestine nature of this kind of research. (By comparison, drone hobbyists have easy access to video, radar and infrared technology, and thus to data.) But it is clear from publicly available military research that one drone, flying alone, cannot reliably track mobile phones below.
Kimberly Hale, who now works as an operations research analyst for the Air Force, provided some insight in her 2012 master’s thesis for the Rand Corporation. She said that the military needed to upgrade its drone fleet to T/FDOA (time/ frequency-difference-of-arrival).108
The accuracy of such a system, Hale writes, will increase with the number of drone patrols used to gather signals. For example, a system of 10 combat air patrols (a minimum of 20 drones) flying at 15,000 feet can track only 20 targets in a country the size of Afghanistan with an accuracy rate of 25 percent. But Hale believes that if the Pentagon could simultaneously fly a minimum of 40 drones (20 combat air patrols) in complementary orbits at 30,000 feet, the Pentagon could reach 95 percent accuracy over Afghanistan.
Even this estimate comes with several caveats, the first being that Hale assumed for purposes of her calculations that Afghanistan was flat. Second, it should be remembered that the higher a drone flies, the lower the quality of the video signal. So the advantage of higher altitude tracking would have to be weighed against the disadvantage of not being able to see the targets. Not least is the significant number of drones needed to fly simultaneously in order to ensure accuracy under Hale’s plan.
Turkish military officer Volkan Tas took a more practical approach in his final thesis for a masters degree in electronic warfare systems engineering at the Naval Postgraduate School in Monterey in 2012. Tas tried to create a mathematical model using geolocation technology to help track Kurdish rebels in the mountains.109
"Civilian and military intelligence has been used at the strategic level to locate [Kurdish forces], but without operational and tactical location systems, success is fleeting at best," Tas writes. "The system should include at least four stationary and one flying UAV [drone] as the fifth receiver for better accuracy."
The problem with this approach is that it needs direct access to ground monitoring sensors, which may not always be available to U.S. troops in Pakistan or Yemen. (For example, the Waziristan mobile network is often turned off.)110 If dedicated interception devices are installed at convenient locations or even mounted on vehicles, this method may work but it will still not be 100 percent reliable.
It should be noted that Predators and Reapers do not carry equipment on board to calculate the location of a phone. Instead this task has to be conducted on the ground by computer systems powerful enough to crunch the data using algorithms like the Interacting Multiple Model to correct for errors in each measurement.
Aware that phone location technologies are only approximate, senior intelligence officials have sought to improve accuracy. A 2009 lawsuit by Netezza, settled out of court, sheds some light on one way the CIA has used complex algorithms to try to pin down target locations. 111
111
Netezza
On September 15, 2009, CompSec, an obscure company in McLean, Virginia, placed an order for Netezza GeoSpatial, a new million-dollar computer system to be delivered to a U.S. government warehouse in Springfield, Virginia. 112
112
Netezza, a multi-million dollar information technology business founded in Massachusetts, sells high-end hardware together with specially configured software. Its on-call technicians provide support and maintenance. While still in development, the new GeoSpatial product had reportedly undergone trials with Japanese mobile phone data and was considered a good fit for other major customers like Canadian Railway and the Dish Network satellite TV which had been shown “proof of concept” versions. 113
113
GeoSpatial was advertised as being able to pinpoint the precise location of users from extremely large data sets stored on Netezza’s new TwinFin hardware. "Until now, decision makers and business users have constantly tried to answer ‘who,’ ‘what,’ and ‘when’ with respect to industry trends, customer and target demographics," declared a Netezza brochure marked “confidential” that was sent to potential clients. "Imagine if the ‘where’ component of every piece of data could be added." 114
114
CompSec was just a go-between for a top secret client—the CIA—which was in a major hurry. "A gentleman named Skip McCormick from the CIA asked us if there was anything we could do to accelerate the development of this," James Baum, the Netezza CEO, would later recall in an April 2010 court deposition. 115
115
McCormick sent Baum an email urging Netezza to speed up its work. "We just upgraded to a [Netezza TwinFin server], but it doesn’t yet have the Geospatial tools," the CIA staffer wrote on October 14, 2009. "I’m trying to figure out what options are available for getting them asap. We depend on the Geospatial tools here every day." 116
116
The problem was that Netezza didn’t make the software the CIA wanted, but hoped to re-sell the spy agency a proprietary geospatial package made by Intelligent Integration Systems (IISi), a small Boston-based company. This software had been licensed to the bigger company for use on the older Netezza Performance Servers but was discovered not to work on the newer TwinFins.
Customers for the original IISi software included Foxwood Casino and the Democratic National Committee which used the software to track gamblers and voters respectively.117 Rich Zimmerman, one of the company’s co-founders, explained in a court affidavit that the software was designed"to incorporate and cross-reference vast amounts of business data with geographic location within the same database, and enable events (such as a tornado heading towards a population center or a mobile phone signal moving from one tower to another) to be matched with personal characteristics in the database - such as telephone numbers for houses in the path of the tornado or the identity of the person whose mobile phone signal has moved from one tower to another - to be mapped and analyzed quickly and efficiently." 118
118
This IISi software was really a business tool to figure out the identity of a user, not a geolocation tool. So when Netezza erroneously marketed the software to the CIA for the drone program, the smaller company balked. "My reaction was one of stun, amazement that they [the CIA] want to kill people with my software that doesn’t work," Zimmerman stated in a court deposition. 119
119
Netezza claimed that IISi had reneged on the terms of the software license, which stated that they would provide technical support. "It was clear that Netezza’s claims were a fabrication—an outright, reprehensible lie," Marshall Peterson, another co-founder of IISi, wrote in an email to Baum and Zimmerman. Peterson, a decorated helicopter pilot who served three combat tours in Vietnam, was one of the developers of a supercomputer named Red Storm, designed for the Pentagon. He had also worked on the development of software for the human genome project. 120
120
The court documents show that Netezza executives and engineers panicked. "No matter how you slice this, we are screwed," Baum wrote to one of his colleagues. 121 The Netezza CEO noted that the company had sold $40 million worth of hardware and software systems to secret, unnamed U.S. government clients in the past year. He was loath to fail on this project, given that Netezza was projecting it could expand federal sales to as much as $100 million the following year.
121 The Netezza CEO noted that the company had sold $40 million worth of hardware and software systems to secret, unnamed U.S. government clients in the past year. He was loath to fail on this project, given that Netezza was projecting it could expand federal sales to as much as $100 million the following year. 122
122
Then IISi sued Netezza, claiming that the new GeoSpatial product was nothing but an altered version of the IISi software— and that it violated the licensing agreement which stated that Netezza would not be allowed to make any changes to the source code. 123
123
In other documents submitted to the court, Matthew Kadillak, a Netezza engineer, testified that he "frequently worked with the government customer in question" and that he helped complete the rush version of Netezza GeoSpatial that was delivered a few days later. 124
124
But tests conducted in mid-October by Sri, an engineer working for McCormick at the CIA, soon concluded that the software could be off by as much as 13 meters (43 feet). 125 By November, Kadillak reported that he, too, was suddenly "seeing lots of errors."
125 By November, Kadillak reported that he, too, was suddenly "seeing lots of errors." 126
126
The two companies came to a confidential out-of-court settlement in November 2010 to drop the lawsuit, soon after IT behemoth IBM bought Netezza for more than six times its expected revenue that year.127
< Previous • Report Index • Download Report • FAQ/Press Materials • Watch Video • Next >



