Drone, Inc. - H. Cross Sensor Cueing
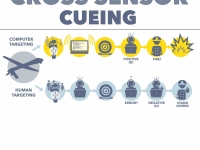
With the bewildering amount of raw data streaming back from multiple sensors on drones, and an array of tools to analyze the information, the Pentagon has been working to simplify and automate target selection. While truly autonomous artificial intelligence systems are still many years away, these new target selection systems are helping remove humans from the killing process.
The Air Force Research Laboratory at the Wright-Patterson Air Force Base has an entire division of research scientists whose task is “sensor management” and the development of “cross sensor cueing” systems that can combine data from multiple sensors to help automatically “cue” i.e., direct aircraft, point video cameras, and launch missiles.128 One such system is the Network Centric Collaborative Targeting System (NCCT), built by ComCept, a division of L-3 Communications.129
The company explains: “ComCept’s multi-intelligence/multi-platform sensor networks greatly accelerate the find, fix, track and target portions of the kill chain, including rapid location of short up-time emitters and tracking of fleeting high-value targets within the target window of vulnerability. Our expertise in data modeling with scalable, distributed network configurations allows for rapid integration of new sensors and capabilities into a common network supporting near real-time tasking and machine-to-machine sensor cross cueing.”130
In essence, this means that when an individual on a wanted target list briefly turns on a listed mobile phone, and as soon an overhead drone or a land tower picks up the phone’s signal, the NCCT system can rapidly send a message to the closest drone video camera and point it toward the phone. An imagery analyst watching this video feed would not necessarily know what technology, systems, or people were involved in tracking the device.
One principal challenge in building such a system was the fact that different types of sensors collect different types of data, meaning that each sensor essentially speaks a different language and cannot communicate outside of that language.
To solve this problem, the Air Force threw out a challenge to come up with a common standard that everybody could use without abandoning their existing systems. “The sum of all wisdom is a cursor over the target,” Gen. John Jumper, then Air Force chief of staff, told the attendees at the April 2002 Command and Control, Intelligence, Surveillance and Reconnaissance conference.131
Jumper’s remark became a mantra: cursor-on-target or CoT for short. It spawned a new uniform data standard to focus multiple sensors on one mission by reducing all targets to just three key variables: what, where, and when. This new standard spawned new software contracts (notably with MITRE Corporation, a Virginia-based, government funded non-profit), academic papers, and even entire conferences.132
This CoT methodology made it easy for algorithms to identify targets and spare human operators the laborious work of comparing multiple kinds of sensor information, such as video, thermal, and phone location data.
But to do this, systems like cursor-on-target oversimplify the problem, throw out any contradictory data, and can end up creating a cart-leading-the-horse approach: They define a target in order to take it out, rather than assess whether the target is even the correct one. This strategy risks producing what statisticians call confirmation bias: the tendency to interpret evidence as confirmation of an existing theory or conclusion.
Ticom Geomatics
Some of the key technology for cueing sensors is made by Ticom Geomatics, a small Austin, Texas start-up founded by a group of scientists who had worked together at another Austin facility - Applied Research Labs, a Navy research facility. 133
133
Ticom sells GEOnet, originally known as ISRnet, which is software that enables a single operator to control multiple sensors from the same workstation, allowing these sensors to work together to geolocate a mobile phone or similar communications device.134 The company specializes in networking sensors to perform T/FDOA, the more complex geolocation method described previously.
“I’m a software technical lead working on an application that coordinates the operation of geographically distributed, heterogeneous sensors and other sensor networks,” Steven Glicker of Ticom announced in a public email post to a World Wide Web Consortium discussion group in April 2006.135 “We must insure that our application will operate with a wide variety of sensors and sensor networks, as well as provide an interface to our ‘consumers’ so they may make effective use of the overall sensing capability without having to deal with specific sensor details.”
The problem is that the geolocation technologies, as we have discussed, can easily be off by several meters. Swapping mobile phone numbers and SIM cards is also common in many parts of the world; locating a phone may not locate the right individual.136 Unless imagery analysts are aware of all these potential error factors leading to their camera being trained on an individual, they are likely to believe that the person in their crosshairs is the person on the kill list, regardless of their true identity.137
Ticom’s software has been adopted by the Marines, Army, Special Operations Command and U.S. intelligence agencies.138 This success has turned the company into hot property. In April 2012, a bigger company, Six3, bought up Ticom for some $60 million. Just 18 months later, CACI, the company made infamous for the interrogators it supplied to the Abu Ghraib prison in Iraq, acquired Six3 for $820 million.139
An Engineer Speaks Out
How accurate is Ticom’s geolocation software? Without access to an independent audit, it is hard to tell, but as in the case of Netezza, there is at least one engineer who claims that the algorithms are inaccurate.
On December 27, 2016, Bernard Henneberger, an engineer who previously worked for Ticom, filed the latest in a series of petitions in what has become a three-year court battle against his former employer. 140
140
The lawsuit alleges two things. First Henneberger claims that he was cheated out of a million dollar stake in Ticom when it was snapped up by Six3 and then by CACI.
The second charge is much more ominous. “I have repeatedly warned Ticom [that] the company’s geolocation technology” could be inaccurate. “This endangers national security and risks innocent lives,” Henneberger wrote and offered to help design a fix. 141
141
Henneberger, who has a master’s degree in signal processing from the University of Houston, was employed for seven years for Lockheed Martin at the NASA offices in Houston where he worked on the Space Shuttle and the Hubble telescope. He went to work for Ticom in 1998, shortly after it was founded by his former co-workers at Applied Research Laboratories at the University of Austin, Texas. 142
142
His filings include news clippings as a stark reminder of the gravity of his allegations. The first was a 2014 Associated Press article headlined “Airstrikes launched amid intelligence gaps.”143 Henneberger later included the front-page copy of the New York Times, containing stories about the 2015 deaths of Giovanni Lo Porto and Warren Weinstein, two Westerners killed in a drone strike while they were held hostage in Pakistan. One of the attached articles is subtitled, “Drone Strikes Reveal Uncomfortable Truth: U.S. Is Often Unsure About Who Will Die.”144
In interviews with CorpWatch, Henneberger confirmed the role of Ticom’s technology, but, after talking to his lawyers, declined to provide any more details.
< Previous • Report Index • Download Report • FAQ/Press Materials • Watch Video • Next >